
How much time have you spent sifting through organization-level data trying to find the right data sets for your specific needs? Not to mention that once you find what you’re looking for, you may find yourself waiting for a centralized IT team to approve your access request – which could take weeks. By the time you gain access, the data is stale and your project is off-track.
While centralized access control decisions will always play an important role in enterprise data security, federating governance to business domains is an increasingly popular way to drive efficiency, establish a data mesh, and derive more value from data.
The question is not necessarily why to do this, but how?
In this blog, we’ll share best practices for defining data domains, and demonstrate how Immuta makes it easy to distribute ownership with domains.
What Is a Data Domain?
A data domain is a container that organizes data based on a categorical grouping or logical organizational structure. Domains allow data management responsibilities to be assigned to a specific business unit, subject matter expert, or team, which alleviates the burden on centralized IT teams to manage data enterprise-wide.
A domain-level approach to data ownership ensures that the users closest to the data dictate how it can be used and by whom. This improves efficiency by ensuring that data use aligns with business needs and is easy to locate. Think of domains as a way to declutter your workspace, so you’re better able to focus on the tasks at hand.
Benefits of Data Domains
Effectively using and managing data assets is a critical imperative for organizations seeking to compete in today’s fast-moving market. As a result, data domains have emerged as a foundational pillar of modern data management strategies. Here are some of the key benefits within Immuta.
Scale Policy Enforcement Across Multiple Organizational Layers
One of the primary advantages of a domain-based approach is the ability to scale data access control enforcement across multiple organizational layers. By defining clear boundaries and ownership for each domain, you ensure that data access is aligned with both business objectives and data compliance requirements.
Enable More Data Policy Creators
Domains put more control in the hands of the people closest to the data, reducing the burden on centralized IT teams. By separating global controls from domain controls, more line-of-business stakeholders are able to author, manage, and enforce policies. Domain owners best understand their domains’ specific needs and requirements, so they can tailor policies and enable more users with the data they need.
Accelerate Data Access and Sharing
By organizing data into domain-specific repositories, you streamline sensitive data discovery and access, eliminating the need to navigate complex data architectures or rely on centralized teams to provision data. Since teams are better able to leverage data, this accelerates time-to-insight and promotes a culture of data-driven collaboration.
Shift to a Federated Model
Data domains allow organizations to manage data security, privacy, and governance at scale in a federated model, such as a data mesh. Aligning data management responsibilities with domain ownership distributes governance and promotes agility, autonomy, and innovation, while maintaining centralized oversight and control. This minimizes the risks of data silos and duplication.
How to Define Data Domains
Data domains clearly have the potential to deliver business benefits. Determining where to begin when defining domains, however, is less straightforward.
When setting out to define your organization’s data domains, start with a central question: Do you already have a governance structure in place?
If the answer is yes, you’re already ahead of the curve. Mimicking your existing governance structure is a straightforward way to define and build your organization’s domains.
If you don’t have an established governance structure, looking at your business operations holistically is a good starting point. A few questions to ask are:
- How are departments and lines of business delineated?
- Are there certain functions that work across all lines of business and others that are more specialized?
- Who are your platform power users, and who uses data less often?
Consider two examples: Company A, a large tech company, offers multiple product lines. Company B, a smaller tech startup, offers a single product.
Company A has dedicated teams for each product line, but other functions – like HR and Finance – span the entire organization. Therefore, it would make sense for Company A to define domains by product line and by function. Within each domain would be multiple sub-domains, as laid out below.
|
|
Product-Centric Domain |
Function-Centric Domain |
|
Primary Domain |
Product Line 1 |
HR |
|
Sub-Domain 1 |
Product Line 1 – Sales |
Recruiting |
|
Sub-Domain 2 |
Product Line 1 – Marketing |
Training |
|
Sub-Domain 3 |
Product Line 1 – Design |
Benefits Management |
By mirroring their internal team structures, Company A’s domains are aligned with business operations, which aids in efficient data use and decision-making.
On the other hand, Company B’s organizational structure is more straightforward. With only one product line, they are able to focus on function-centric domains. Depending on the volume of data assets and users, as well as plans for future growth, Company B may also have sub-domains to manage data access at a more granular level.
How to Define Domains Using Immuta
With Immuta’s Domains capability, you’re able to easily define data controls at the enterprise and domain levels, giving data owners control and visibility into how their data is utilized. Incorporating logical organizational structures into access control decisions makes those decisions much more straightforward and efficient, without impacting or disrupting other teams.
Below is a step-by-step look at creating and operationalizing Domains in Immuta.
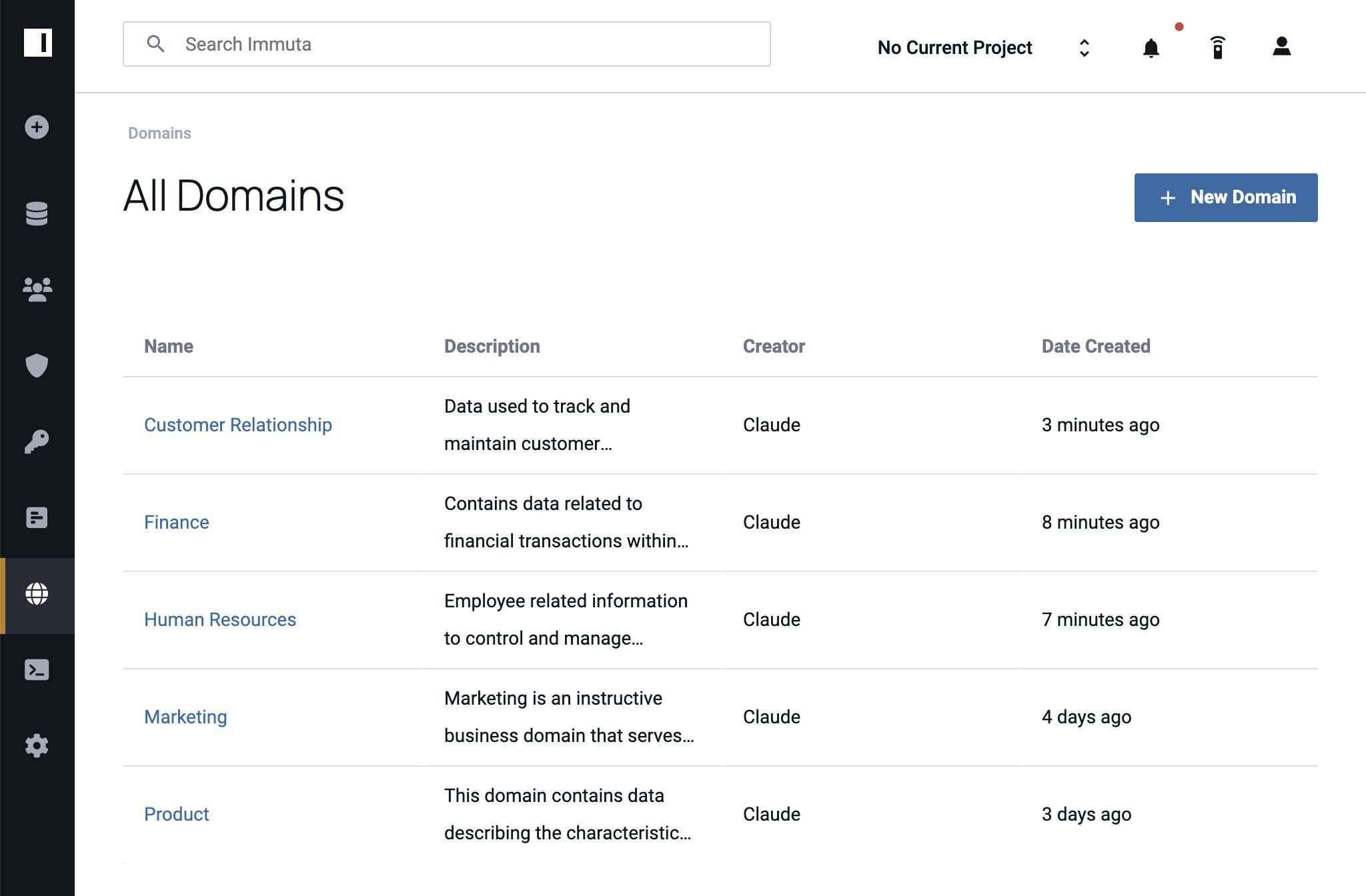
1. Create a Domain
To get started with Immuta Domains, users with the Governance permission navigate to the Domains page and click + New Domain. After adding a domain name and description, the governor clicks Save and can begin adding data sources.
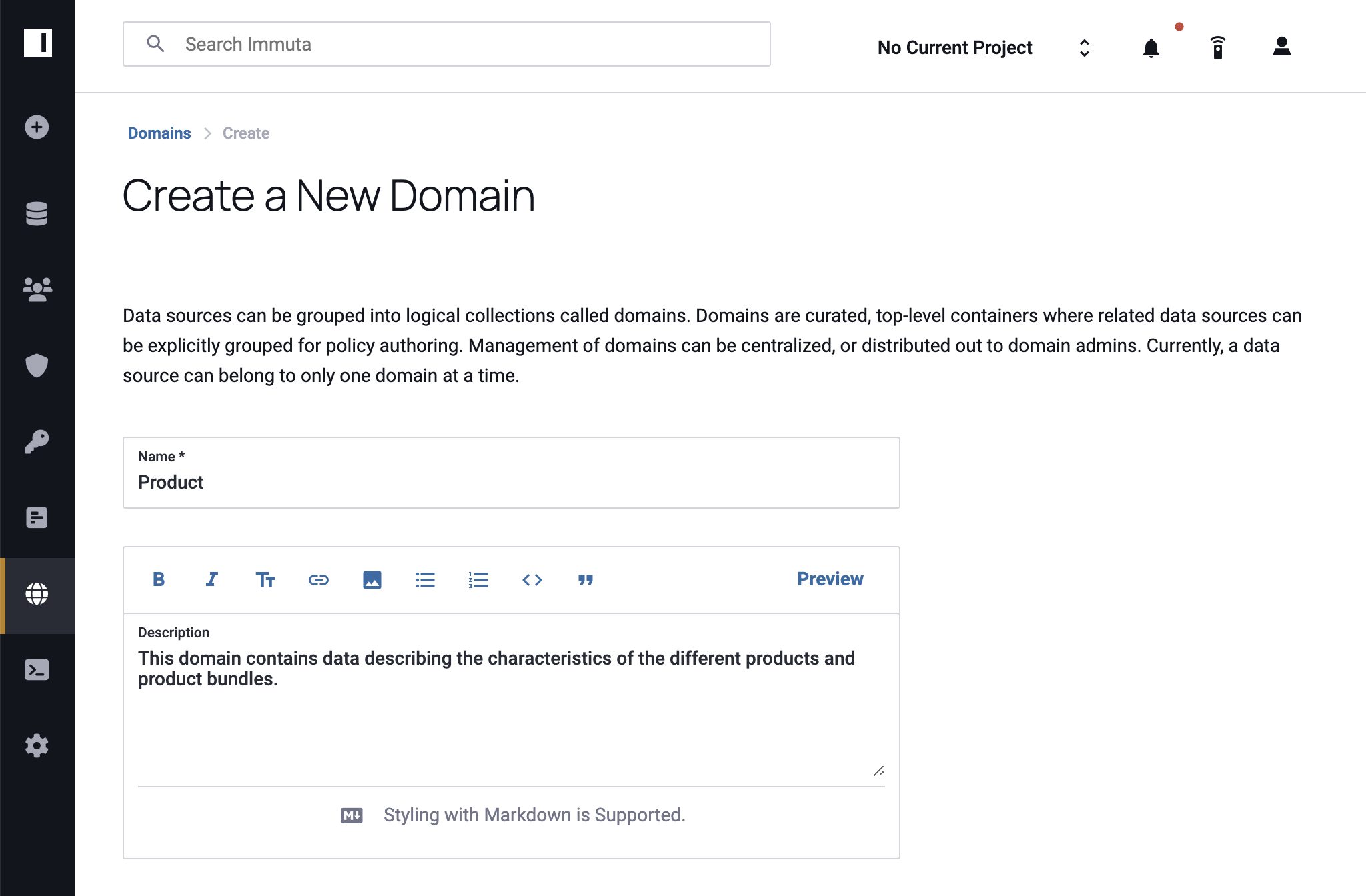
2. Assign Permissions
User Admins in Immuta navigate to the Domain Permissions tab or the People Page to assign policy management permissions to domain users, either individually or in groups. Drawing on our earlier example, you might add individual users from different teams to a product-centric domain, but for a function-centric domain you would bulk add all the users from that function who will have policy management responsibilities.
Once users are added, click the Manage Policies permission so that they are able to create and apply policies within the domain. After you’ve reviewed your updates, click Grant Permissions to save them. Permissions are editable and displayed under user and group admin pages for quick reference and future updates.
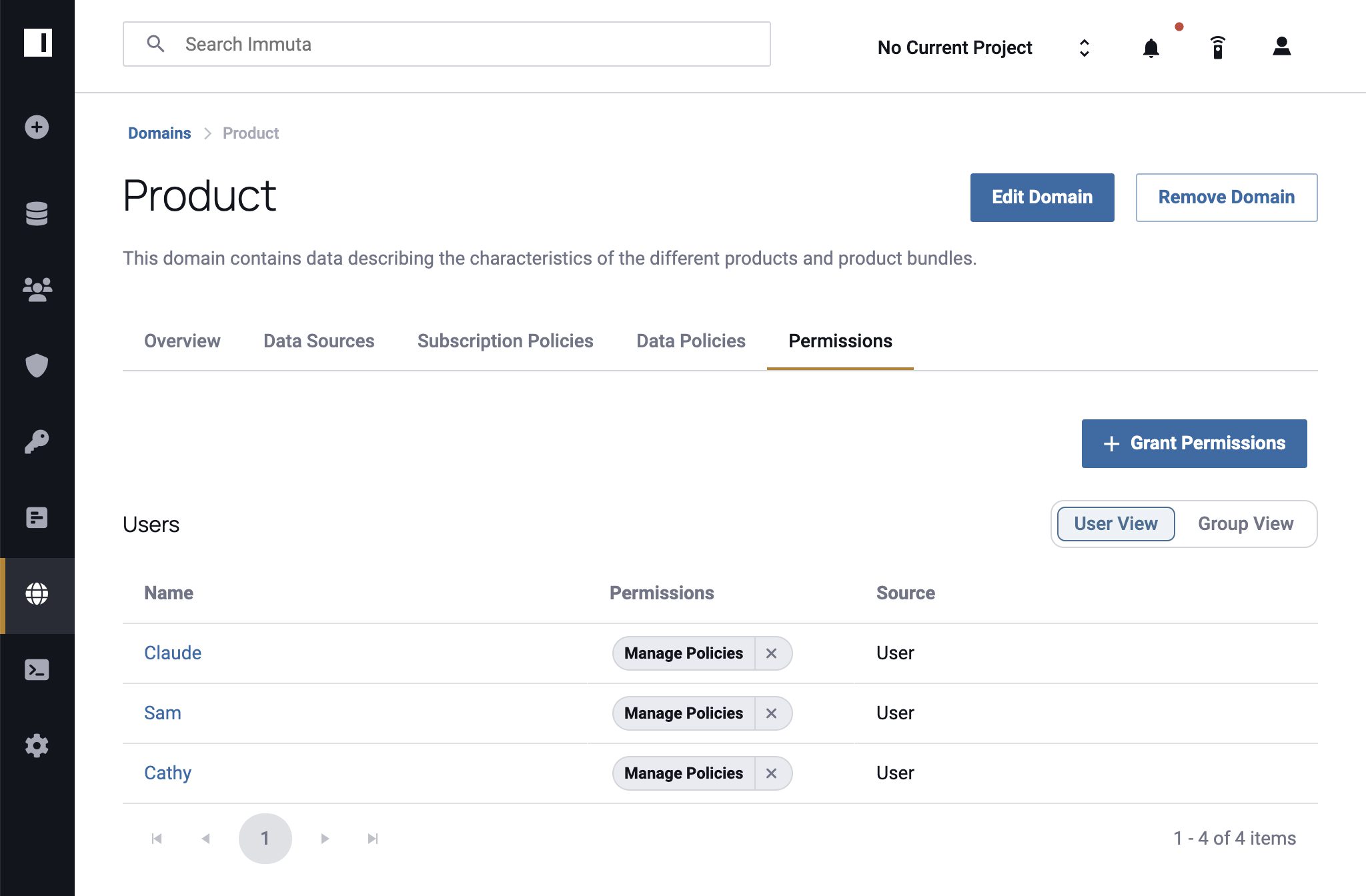
3. Add Data Sources
Next, add data sources to domains based on business units, goals, or policy management structures. In this step, Immuta users with the Governance permission enter the domain’s Data Sources tab and click + Add Data Sources to select the data sources needed for that domain. Once all the necessary boxes have been checked, click + Add to Domain to finalize.
Data sources can belong to more than one domain at a time, which allows you to create pseudo-subdomains or products. For instance, a Product Management domain and a Research domain may have access to the same research data source, albeit for different purposes. Additionally, a user with the Governance permission can assign User Admins the ability to manage policies within a given domain.
4. Create & Enforce Policies
The most important step – and the one that makes Immuta Domains a powerful tool across functions – is to implement policies to protect your data. Immuta users with the Governance permission, or those who were given the Manage Policies permission in step 2, will select the appropriate domain from the Domains page and navigate to either the Subscription Policies or Data Policies tab.
It’s important to distinguish between subscription and data policies:
- Subscription policies grant users access to data objects such as tables or views.
- Data policies restrict how people can access data by redacting columns or rows.
While these policies serve different functions, both are integral for fine-grained access control. For instance, you can grant a group of users access to a table within a domain using a subscription policy, then restrict sensitive rows for users who aren’t authorized to see that information using a data policy.
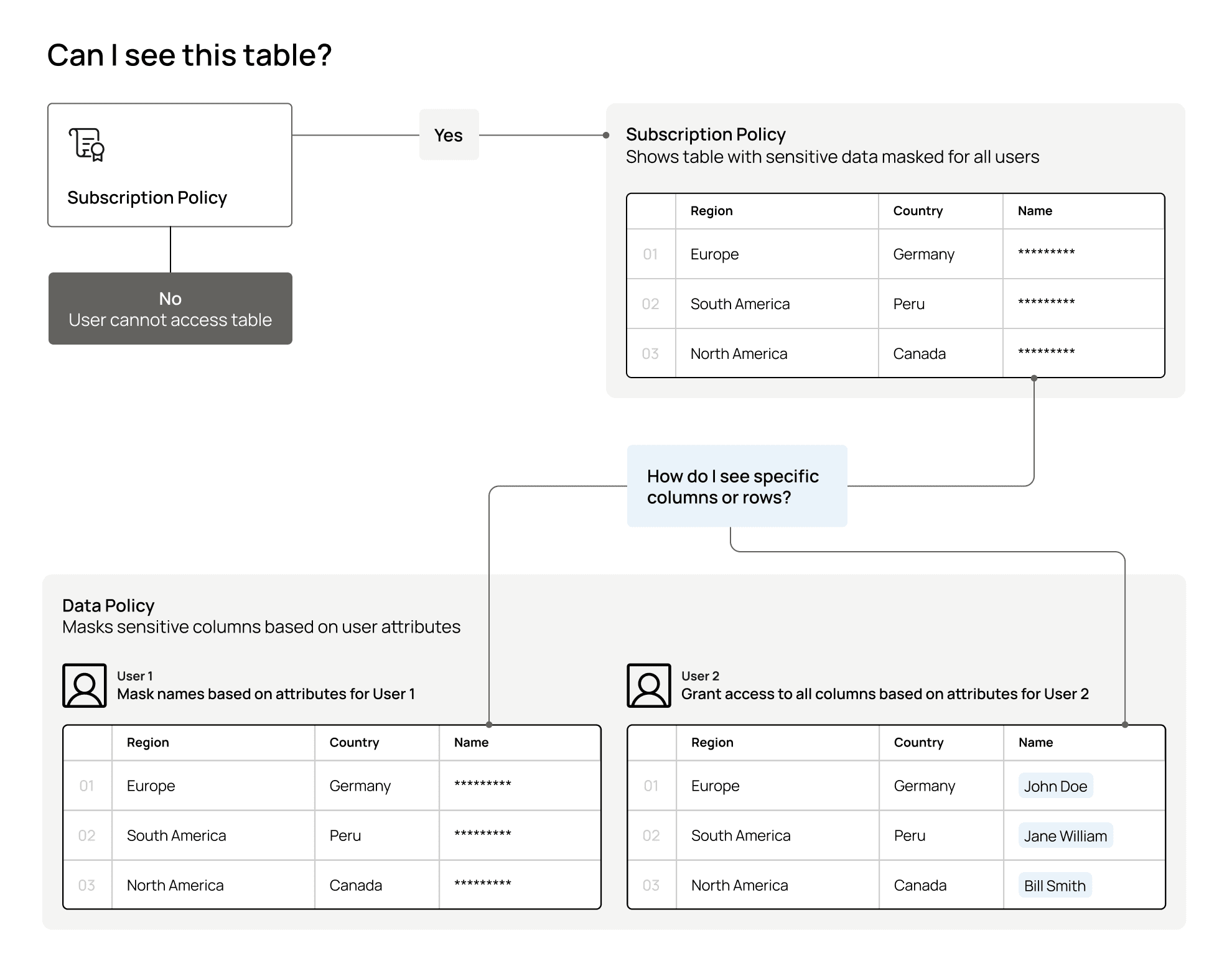
To ensure that it’s clear which domain a policy should be enforced on, there is a section in the policy builder to select the correct domain. Note that the Manage Policies permission allows you to select multiple domains. Once created, the policy will apply to all data sources within the selected domain(s).
Start Defining Data Domains
As more organizations move toward distributed ecosystems and decentralized governance models, defining data domains will be critical to stay agile, flexible, and scalable. Immuta Domains makes it easy by mirroring existing hierarchies and aligning policy management to them.
Defining policies at the domain level gives you greater visibility into who is responsible for data management across functions, who has access to specific data sources, and what they’re allowed to do with that data. This simplifies auditing for compliance while reducing the burden of responsibility on centralized IT and governance teams. There is also no disruption for users – they can only see domains that they’ve been granted permission to, which reduces confusion and analysis paralysis.
As a result, you’ll improve process efficiency, accelerate time to data, and generate accurate, domain-specific insights, with no additional overhead or bottlenecks.
“Being efficient with data while also being smart about data security is key for us. That’s why we’re excited about Immuta’s new Domains capability,” said Itzik Feldman, Senior Engineering Manager, Analytics Platform at Atlassian. “With our business domains able to set their own policies, we can de-risk data with confidence in how it’s being used, without excessive delays or red tape. For Atlassian, that means greater efficiency, productivity, innovation, and ultimately, value.”
To read more about Immuta Domains, read our Domains Reference Guide or watch the demo below.
Starting Securing Data Domains
Get in touch with our team.









