2022 Data Access & Analytics Trendbook
Expert perspectives on where data use is heading


When it comes to making decisions, context is essential. Imagine your neighbor asks for a key to your house. If they’ve agreed to watch your dog while you’re away on an upcoming business trip, this question should present no issues or concerns. If they’re asking because they want to throw a massive party that ends up on the news, you probably won’t want to fulfill their request.
In this situation, the driving factor in your decision to share the key is the purpose for which it is being used. The decision is entirely determined by context. Without these details, you’d have no idea as to what your neighbor intends to do with the keys to your home.
This need for context is equally as important in the world of data. Knowing why a user is requesting access to a data set is just as important as their title, role, or any other identifying attribute. It gives the person tasked with granting or restricting access the information they need to make the right decision.
Purpose-based access control, which we will refer to as PBAC, is a method of data access control that makes access decisions based on the purpose that a given user or tool intends to use the data for. These purposes can include running a report, performing an audit, creating a new application, and much more. The variety of purposes provides flexibility with which data governance teams can build a high-powered, granular access control model.
On the spectrum of access control methods, PBAC is closest to its direct forerunner attribute-based access control (ABAC), which determines access based on a range of dynamic attributes specific to individual users, data, and the data environment. The key difference is that ABAC grants access based on this range of identifying attributes, while PBAC grants access based on the defined purpose for which the request is being made. Purpose is determined separately from identity, and it can be applied universally across an organization’s data ecosystem.
That being said, the distinct nature of PBAC and ABAC does not mean they’re mutually exclusive. In fact, these access control models can be implemented simultaneously in order to facilitate access decisions based on both dynamic attributes and contextual purposes.
PBAC, as the next step in the evolution of access controls, has merit as an important part of modern data access systems. Not only does it provide more measurable context on which to determine accessibility, but it also gives organizations that extra level of control against risk. Other than the general utility of PBAC, however, why is it so important?
One of the most popular and relevant use cases for PBAC is achieving compliance with many of today’s data privacy laws and regulations. Most of these regulations, including staples like GDPR and HIPAA, involve purpose clauses that require sensitive data only be collected and used for precise reasons.
For example, the GDPR’s Purpose Limitation Principle states that “Personal data should only be collected and processed for a legitimate specific purpose.” Furthermore, the regulation claims that the specific purpose “should be expressed in an unambiguous, transparent, and simple manner” in order to be compliant.
The goal of this clause is to ensure that sensitive information is not being unnecessarily collected, stored, and exposed to risk by organizations that use it. With PBAC, organizations can exhibit the granular, purpose-based control over data access that ensures compliance with these standards.
There is another form of contemporary access control that is sometimes referred to as “PBAC”: policy-based access control. It’s important to clarify that, while often referred to by the same acronym, these two access control methods are not the same.
To reiterate the distinction between the two at the control enforcement level:
Ultimately, the term “policy-based” is becoming outdated in the face of the evolution of access control models. Since ABAC and its predecessor role-based access control (RBAC) are both policy-based, this terminology is broadened to the point of non-specificity. That is why we use PBAC to discuss access based on purpose, not policy. The policy-based access controls of yesterday are evolving alongside the data they govern and are incorporating more contextual information into access decisions, driving toward a future where purpose is vital.
[Tip] For more on the history and evolution of access control, read our free white paper.

Expert perspectives on where data use is heading
Now that we understand what PBAC is (and what it’s not), we can examine how it works in practice.
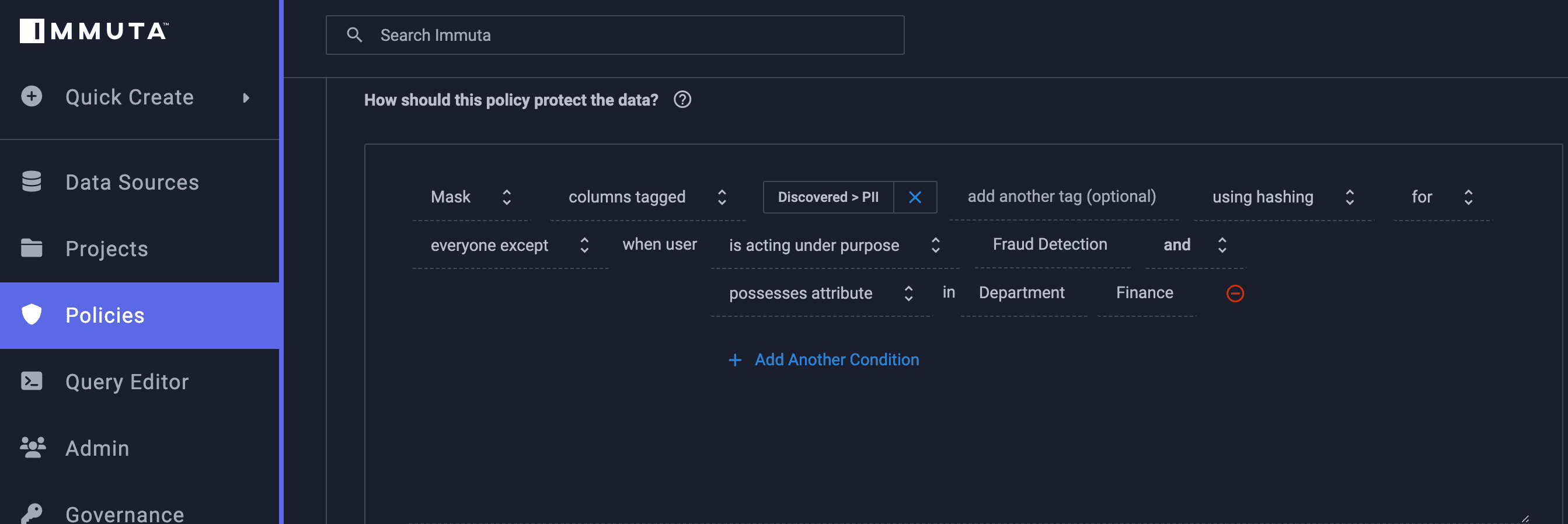
Let’s imagine that you work for a data governance team at a financial institution. Much of the data you’re collecting from your customers, whether it be credit card numbers or bank account information, is extremely sensitive. This makes it all the more important that this data is kept safe from risk of leak or breach. Using ABAC to determine access will help determine which data users are able to see which information based on their given attributes. But what if an exception needs to be made to a global policy in order to enable data collaboration that would normally be restricted for certain users?
This is where having a purpose-based layer of access control is key. This user, who may not normally have access based on their attributes, could be assigned a specific purpose that alters their permissions. For instance, if they’re part of the organization’s legal team, they probably won’t typically have attribute-based access to credit card transaction data. But if a fraud case requires legal oversight and input, this user could be assigned a “fraud detection” purpose that (in a compliant fashion) grants them access to this information for this specific reason. This purpose could be rescinded after the case was closed, and the data would once again be hidden from this user.
[Tip] Click here to see PBAC and ABAC working in action to mask sensitive data.
As evidenced in this example, PBAC can be extremely effective when applied in tandem with dynamic ABAC. Between ABAC’s flexibility and PBAC’s enhanced context, these two forms of access control can be combined to create a model that is both scalable and secure.
Immuta’s Data Access platform makes access decisions based on user, data, and environmental attributes as well as contextual purposes. By leveraging both ABAC and PBAC, Immuta enables automated data policy enforcement on the most sensitive data, and helps prove compliance through a consistent audit log. Purposes in Immuta must be pre-approved by legal teams, and users are required to acknowledge a purpose statement before they can access sensitive data. Immuta makes certain that the right users have access to the right data at the right time – so long as it’s for the right reasons. Adding this element of purpose-based context is the most effective way to determine whether or not the reason is legitimate.
Want to see Immuta’s policy enforcement in action? Try out our new self-guided walkthrough demo!
Innovate faster in every area of your business with workflow-driven solutions for data access governance and data marketplaces.