Immuta is the modern data security platform that gives you the power to leverage metadata to build and automatically enforce access policies and apply dynamic data masking techniques at query time. These capabilities make Immuta a seamless fit with Alation, which many customers rely on as their enterprise-wide data catalog solution. Put simply, Immuta allows you to maximize your existing investment in Alation by enabling metadata operationalization for safe data analytics use.
In this blog, we’ll take a deeper look into how Immuta and Alation work together, with a step-by-step guide to implementation.
Why Do Alation Customers Adopt Immuta?
Data stewards working in Alation are primarily responsible for creating and maintaining policies, but the onus is on data architects and engineers to ensure the necessary policies are implemented and continuously enforced on their cloud data platforms, such as Databricks and Snowflake, for compliant data use. Additionally, data access control policies must account for real-time changes to data, roles, purposes, or other dynamic attributes.
Immuta provides a data security and governance layer that can be integrated with metadata from Alation to automate controls and enforce enterprise policies for data analytics. That way, if there are assets or elements that should not be used or leveraged by certain analysts, those analysts are not necessarily fully blocked from the data; instead, they are able to query a resource and receive an appropriate level of insights while still retaining, masking, or obfuscating objects that shouldn’t be accessed or viewed. All of this is done automatically at query time, so that analysts still receive quality data, with the caveat that it is amended for their specific needs and permissions.
With this fine-grained access control, organizations leveraging Immuta with Alation are able to accelerate safe, self-service access to data without burdening multiple parties throughout the organization with policy implementation management. What specific capabilities does Immuta offer to data platform and engineering teams looking to operationalize metadata in Alation?
| Discover & Classify | Data Catalog | Data Access Control | Data Masking & Privacy | |
|---|---|---|---|---|
| Alation | Alation automatically classifies and tags sensitive information, and maps it to the appropriate privacy policies. | The Alation data catalog inventories data and collects metadata on usage that is leveraged to embed governance into data consumers’ daily workflows and activities. | ||
| Immuta | Immuta’s sensitive data discovery also automatically discovers, classifies, and tags structured data for simplified policy enforcement. | Fine-grained attribute-based access control allows you to manage access control policy enforcement across all cloud data platforms without having to move or copy data, or manage hundreds of roles. | Immuta’s dynamic data masking capabilities include hashing, conditional data masking, k-anonymization, randomized response, and obfuscation, allowing you to avoid manual anonymization or masking approaches. |
You can watch an example of how Immuta and Alation work together in production in this on-demand webinar presented by the Director of Enterprise Architecture at Aon.
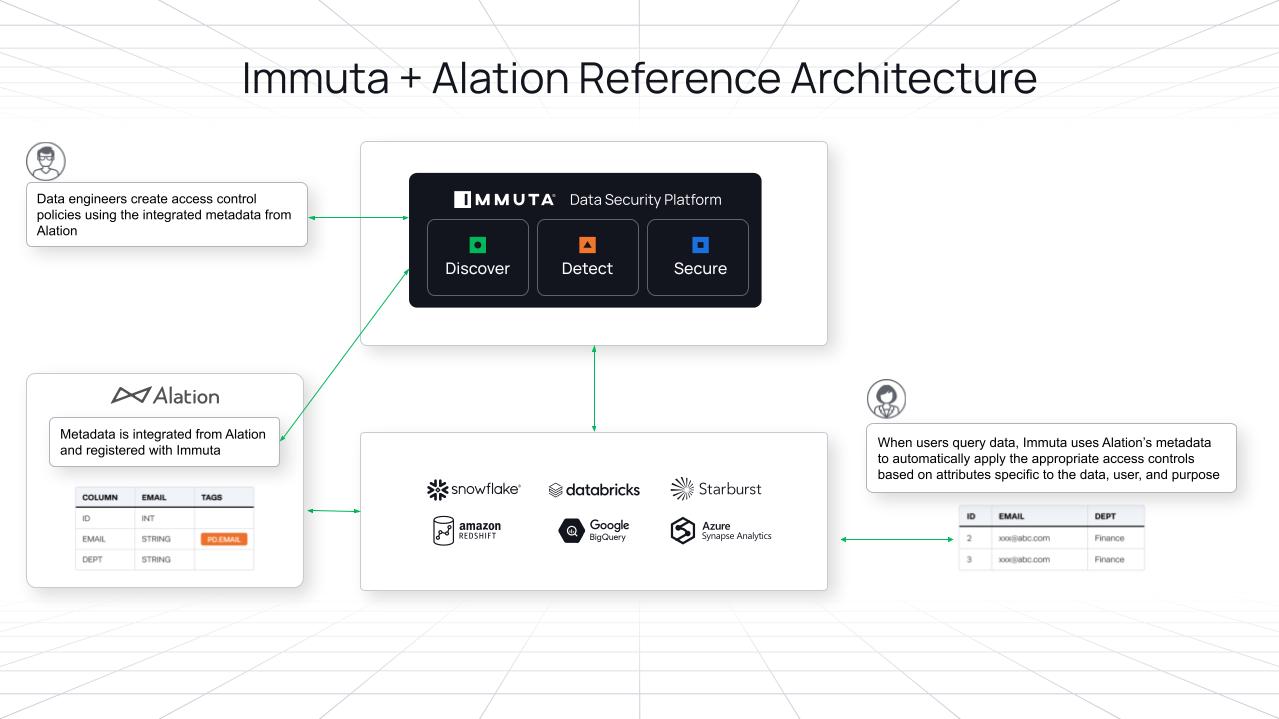
How is Immuta Implemented with Alation?
- Tags and Custom Fields from Alation are linked to Immuta Tags. Note that Alation Tags are not permissioned, but Custom Fields do have access controls.
- Data engineers/architects create access control policies using the integrated metadata from Alation.
- When users query data, Immuta uses Alation’s metadata to automatically apply the appropriate access controls based on attributes specific to the data, user, and purpose.
- Data consumers are only able to access/use data at the level appropriate for their user entitlements.
Steps to Integrate Alation as an External Catalog with Immuta
- Click the App Settings icon in the left sidebar..
- Click the External Catalogs link to navigate to that section.
- Click the button to “Add Catalog,” set a Display Name of your choice, and select the Catalog Type “Alation.”
- Enter your URL and API Key, choose to link Tags and/or Custom Fields, then click Test Connection. Then click the Save button

5. Create data access policies driven by Alation metadata that are enforced transparently for data consumers using their favorite cloud data platforms such as Databricks, Snowflake, Starburst, Amazon Redshift, Google BigQuery, Azure Synapse, and more.
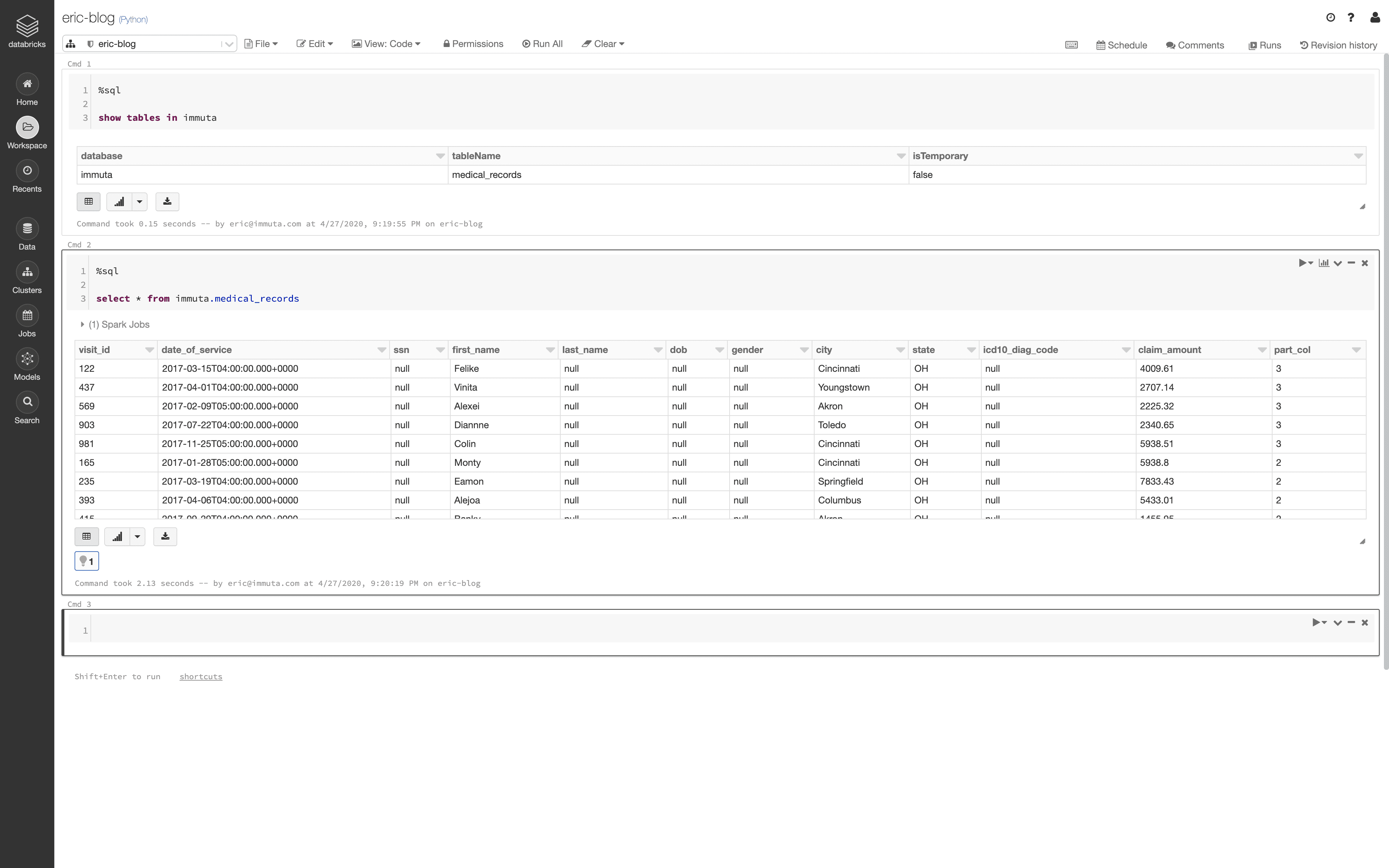
How Can Data-Driven Organizations Benefit from Alation with Immuta?
Within Alation, metadata and data usage are mutually beneficial: The more data consumers use Alation, the better its metadata becomes, and the better its metadata becomes, the easier it is for users to find data. Adding Immuta to that cycle helps ensure that the right data is accessible to the right people at the right time, based on metadata-informed access control policies.
Leveraging metadata to automatically enforce these policies at query time removes the burden on data engineers and architects, as well as other stakeholders throughout the organization, to manually monitor policy implementation. Now, data users will not be prohibited from accessing data that doesn’t map to their role, but rather will see data with the appropriate level of insight based on dynamic attributes like usage purpose, data type, time, and more.
This continuous enforcement on cloud data platforms applies to any data consumer, whether accessing data from data science notebooks, analytical tools, or through Alation Compose, and it further reduces the need to use manual workflow steps to request or deny access to sensitive data.
Immuta and Alation’s proactive approach to data security simplifies the responsibilities of data engineering and DataOps teams while making data access seamless and secure for all users. Hear it firsthand from Alation VP of Market Strategy, Mitesh Shah, below, and visit our documentation site to learn more.